Data protection in Cyber security
In this post learn What is meaning of Data protection is, the types, and objectives, the Eight Standard Principles of Data, and How to Ensure Compliance In Data Protection.
Difference between Data Privacy and Data Protection
Data privacy defines who has been authorized to have access to data, while data protection provides tools and policies to actually protect and restrict access to the data.
What does data protection mean?
Data protection is the process of safeguarding data from unauthorized access or loss to secure the privacy, availability, and integrity of your data.
Data Protection Act, 2012:
lays down rules we need to follow in collecting, using, disclosing, or handling personal data or information by a data controller or processor.
What is the difference between data controller and data processor?
Data controller and Is an organization or entity responsible to determine why and how data Should be collected. whiles The Data processor: is the entity responsible for processing data on behalf of the Data controller.
What are the types of data protection?
• Data Encryption
• Data Backup to The Cloud
• Password Protection
• Identity And Access Management
• Intrusion Detection and Prevention Software.
What is the role of the Data Protection Commission?
The data protection commission is an independent statutory body to ensures compliance with data protection.
• Protecting the privacy of an individual and their data
• Providing a process to collect, hold, use or disclose personal information.
What does data protection law applies
The data protection law applies to all forms of personal data or information stored on both electronic and non-electronic platform.
The Act lays down specific penalties for various situations such as failure to register as a data controller, however, in case a person commits an offense under this act for which a penalty is not specified, the person is liable to
• A fine of more than five thousand penalties unite
• A term of imprisonment of not more than ten years or
• Both
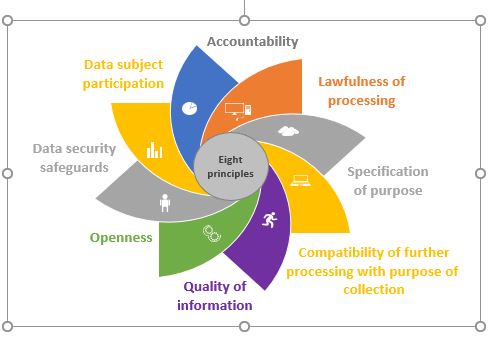
Eight Standard Principles of Data Protection
The act established eight standard principles which must be complied with by anyone who processes personal information across the country and beyond
Accountability: This is whereby the Data controller or processor is accountable to the person who collects his or her information if there is a breach in data collecting.
The Lawfulness of Processing: After collecting the data we must use a lawful way to process the data not a wrongful process of information.
Specification of purpose: Let the customer know the purpose of collecting the data
Processing with Purpose of Collection: The information collector must be used for the actual purpose or the main reason for data collection.
Quality of information: The collection of customer data must be accurate, complete, and free from errors.
Openness: When the data is collected and there is a breach of privacy on customer information, informed the client.
Data Security Safeguards: After collecting the data there should be proper security control to protect the Data.
Data subject participation: When collecting the data from start to finish you must involve the person whose information or data has been collected.
How to Ensure compliance In Data Protection
• Register with the DPC
• Renew the registration every two years
• Officially appoint a data protection supervisor (Give job schedule)
• Train data protection supervisor
• Conduct data protection gap analysis
• Remediate identified gaps
• Establish and implement data protection policies & procedures
• Conduct data protection awareness and training for employee
Again, You can read on Overview of Cybersecurity in Organization ,Cybersecurity in Banking Fraud,Cybersecurity Incident Response Plan and Threat Intelligence in Cybersecurity.
I will also recommend you read the post on How Does Cloud Computing Technology Work, Turn ON or Off Two Factor(2F) Authentication for your Gmail using your Phone Number, Add alternative Email or Phone to Reset Account Password in the event of forgetting your Login credential and How to Login to Gmail Account, Sync Phone contact, Export Contacts from Gmail Account to Phone it cold be of help.
Conclusion
Now, you must have an idea of Data protection in Cyber security. Ask your questions in the comments below. Try to follow us on Facebook, Instagram , and Twitter. Also if the post has helped you Kindly subscribe to our YouTube channel to continue learning.

