Threat Intelligence in Cybersecurity
As a business continues to evolve and provide its service through information technology to ensure business operations. there should be intelligence mercantilism used to gather analytical data to understand past, current, and future threats are essential. This will enable them to come out with Solutions and use them to identify any security breach and recover in the event of cybersecurity threats. This article will lay out what is threat intelligence, Threat intelligence, and the process that Helps in Threat intelligence.
What is threat intelligence in cyber security?
Threat Intelligent refers to the information used by an organization to better understand past, current, and future threats. Threat intelligence provides the context necessary to make informed decisions about your network security, especially after an attack has occurred.
Why is threat intelligence important?
• Loss of Data Prevention: With well-structured cybersecurity intelligence, organizations can spot cyber-attack and prevent sensitive data breaches.
• Provide direction on safety measures: It ensures organizations put security measures in place to safeguard in the event of cybercriminals attack in the future.
• Collative collaboration: A well-structured cybersecurity intelligence Helps experts to Share experience with colleges in the event of cyberattacks and plans to mitigate or fight cybercrimes, as cyber threats keep growing at a rapid pace.
What are the three types of cyber threat intelligence?
• Strategic: It uses detailed analyses of trends and emerging risks to create a general picture of the possible consequences of a cyberattack. Simply put, it asks the question: “Given our technical landscape, what’s the worst that can happen?” This information is often presented to high-level decision-makers within an organization, like board members
• Tactical: outlines the tactics, techniques, and procedures of threat actors. It should help defenders understand, in specific terms, how their organization might be attacked and the best ways to defend against or mitigate those attacks.
• Operational: It helps organizations understand the possible threat actors and their intention, capability, and opportunity to attack vulnerable IT assets, and also the impact of the attack is carried out.
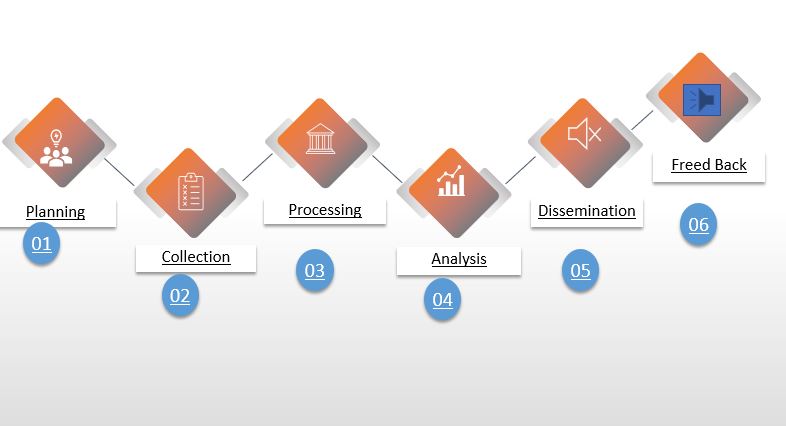
What are the threat intelligence cycle steps?
1. Planning and Direction
The first step is to decide the main goals and tasks for threat intelligence and ask the right question.
• Understanding your intelligence objectives based on factors like how rules and regulations have been followed at your organization’s
• Identifying how threat intelligence improves operational efficiency for the department?
• Understanding what threat intelligence is, the organization needs to Identify and protect assets and respond to threats.
2. Collection
The second step is to gather raw data to support the requirements set in the first stage. It’s best to keep track of network event logs and records of previous incident responses and identify external ones from the open web, social media websites, and technical sources.
3. Processing
Once all the raw data has been collected, you need to sort it, group it with metadata tags, and filter out multiple information.
4. Analysis
The next step is to process the information gathered there to make meaning of the processed data. The objective of the analysis is to search for potential security threats that the organization can use to fulfill the intelligence requirements layout.
5. Dissemination
After analysis, it has to communicate to get to the right people at the right time.
– It also needs to be followed so that there is business continuity
6. Feedback
Is the final step being when the threat intelligence cycle? feedback from people will help improve the threat intelligence in the organization that will helps in producing accurate intelligence through timely assessments.
Again, You can read on Overview of Cybersecurity in Organization ,Cybersecurity in Banking Fraud and Cybersecurity Incident Response Plan. I will also recommend you read the post on Data protection in Cyber security, How Does Cloud Computing Technology Work, Turn ON or Off Two Factor(2F) Authentication for your Gmail using your Phone Number, Add alternative Email or Phone to Reset Account Password in the event of forgetting your Login credential, How to Use Google Translate and How to Login to Gmail Account, Sync Phone contact, Export Contacts from Gmail Account to Phone it could be of help.
Conclusion
Now, you must have a Threat Intelligence in Cybersecurity. Ask your questions in the comments below. Try to follow us on Facebook, Instagram , and Twitter. Also if the post has helped you Kindly subscribe to our YouTube channel to continue learning.

